Posted by Sander Berkouwer on October 14th, 2010 |
0 commentsServer Core installations were a new feature in Windows Server 2008. Now, in Windows Server 2008 R2, it has been given a major upgrade. It now includes the .Net Framework, Active Directory Certificate Services, etc.
Over three years ago I showed you how to install a Server Core Domain Controller in Windows Server 2008. A lot of people found this useful information. So, with Windows Server 2008 R2 looking towards Service Pack 1 (SP1), I thought I’d show you how to install Server Core R2 Domain Controller.
The process to install a Server Core R2 Domain Controller differs somewhat from the installation process of a Windows Server 2008 Server Core Domain Controller.
This blogpost explains the differences, by walking through the process:
Step 1: Install the Operating System
Step 2: Configure basic settings
Step 3: License the Server
Step 4: Update the Server
Step 5: Install the roles and features
Step 6: Install additional features
Step 7: Update the Server
Step 8: Run the Best Practices Analyzer
Step 1: Install the Operating System
Before you install any Operating System on any box, make sure you upgrade the BIOS and any applicable firmware to the latest stable version. Also make sure the box meets the minimum hardware requirements for Windows Server 2008 R2:
- One 1,4 GHz x86-64bit capable processor
- 512 MB RAM
- 32 GB free hard disk space
Although, these system requirements will allow you to install Windows Server 2008 R2, it’s practical to insert a DVD player to read the DVD, created using the ISO file for Windows Server 2008 R2.
Installing Windows Server 2008 R2 is a simple process. Simply boot from the DVD and perform the following steps:
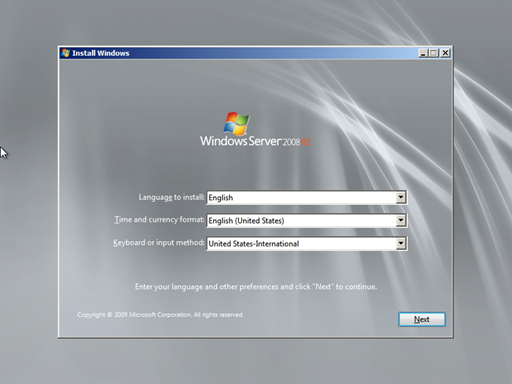
In the Install Windows screen select the Language to install, Time and currency format and Keyboard or input method. When done, click Next.

In the second Install Windows screen, click on Install now.
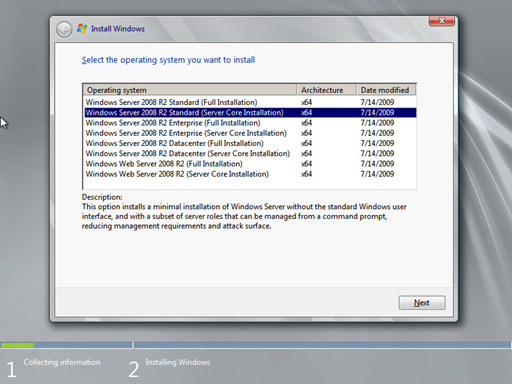
In the Select the operating system you want to install screen, select Windows Server 2008 R2 Standard (Server Core Installation) from the list.
Note:
In some environments the Enterprise edition might be recommended, based upon the needs of the organization. Check this blogpost to make a decision between Windows Server Standard Edition and Windows Server Enterprise Edition.
When done, click Next.
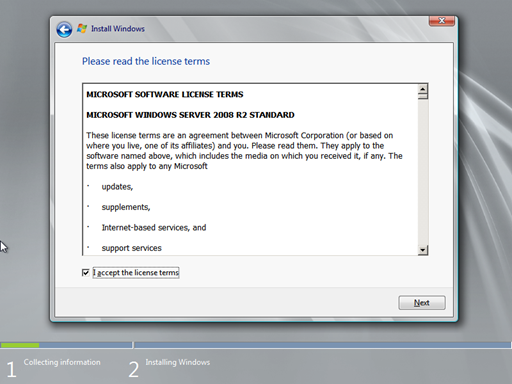
In the Please read the license terms screen, select the I accept the license terms option and click Next. If your curious about the license terms or want to know how you’re selling your soul to Microsoft, you might want to read the whole license terms.
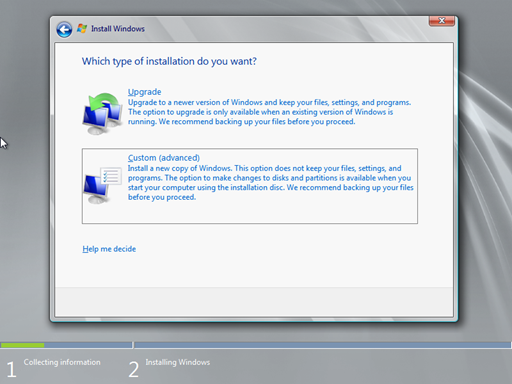
In the Which type of installation do you want? screen, select the Custom (advanced) option. This will install a new copy of Windows. This option does not keep your files, settings and programs.
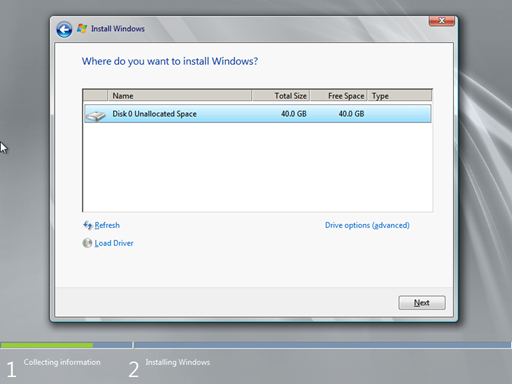
The final question in the Windows Server 2008 R2 installation process is Where do you want to install Windows? Since this is a new box, the built-in 40GB disk will do.
Tip!
It is a best practice to place dynamic data on a different partition than the system partition in Windows. You might want to partition the disk to dedicate room to the Active Directory Transaction Logs, Active Directory database and System Volume (SYSVOL). For more information, look here.
Now, Windows Server 2008 R2 will install on the system.
Step 2: Configure basic settings
Once your Server Core installation is complete (this should only take about 10 minutes), you’re presented with the logon screen.
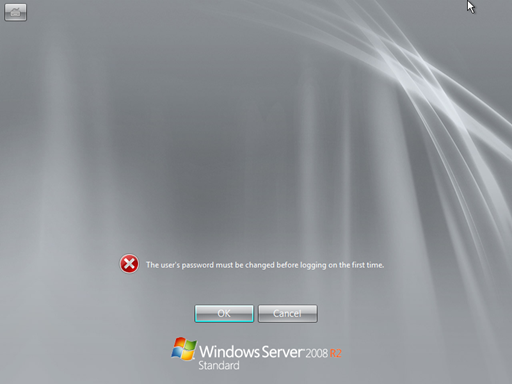
The first time you log on to Windows Server 2008 R2 you need to change the password. Press OK, than enter a new password twice and press the orb. When done, click OK to acknowledge you now have a password.
Note:
The password needs to comply with complexity requirements.
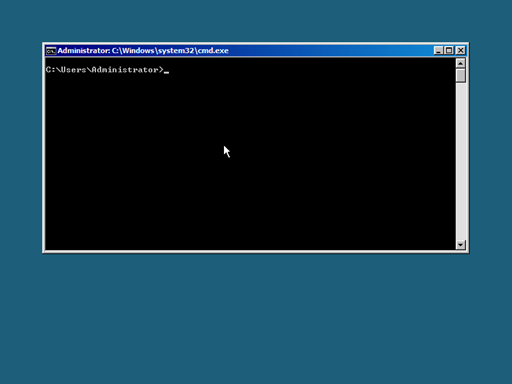
Congratulations! You are now at the console of a Server Core installation.
Let’s configure the box with some basic settings, like a computername you can actually remember and some IP settings to fit into your current environment. To this purpose we’re starting up sconfig.cmd.

With this built-in Server Configuration tool, you can easily see and change settings. As you might notice at a first glance, the server is autonamed. Let’s change the computername.
Press 2, Enter and then Enter new computer name (Blank=Cancel). I decided to name this server SCDC1. After pressing Enter, you will be confronted with a message stating the computer needs to be restarted to apply these setting. Press Yes to reboot.
After the reboot, log on with the password you provided earlier.
Now we’re ready to insert some meaningful IP information. Start up sconfig.cmd again and choose option 8) Network Settings. by typing 8 and an Enter. This will land you in the Network Settings menu.
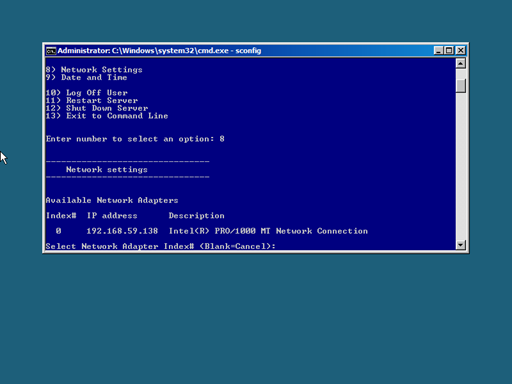
For this blogpost I’m using a system with a single Network Interface Card (NIC). The IP address in the screenshot has been assigned by DHCP.
Note:
An Active Directory Domain Controller, however, needs a fixed IP address to be able to register it’s A and SRV records.
Note:
In Server Core installations of Windows Server 2008 and Windows Server 2008 R2, IPv6 is disabled by default.
When in the Network Settings menu of the Server Configuration tool, press the index number of the NIC you want to modify. (in my case 0) Then type 1, followed by an Enter to access the menu where you change the IPv4 address. Type S and Enter to specify a Static IP address. Then, type the IPv4 address for the server. In my case I’ll use the 192.168.59.10 address, which I enforce with Enter. The default Subnet will do in this case, so I’ll accept it with Enter. As my Default Gateway (the nearest router) I choose 192.168.59.2. An Enter completes this submenu.
The server now has a static IPv4 address. It, however, does not have any DNS Servers configured, so in the Network Settings menu for the NIC, type 2, followed by an Enter. Now type the IPv4 address of the primary DNS Server you’d like to use. Press Enter when done. Click on OK in the message stating “Preferred DNS Server set”. If you want to set a secondary DNS Server you also have the chance. I cancelled out on this by simply pressing Enter.
Step 3: License the Server
Now, our Server Core Domain Controller is able to communicate with the network.
Let’s enter the Windows Product Key for our system to continue to enjoy its bountiful commandline.
Type the following two commands to license the server with a KMS host:
start /w slmgr.vbs -ipk YC6KT-GKW9T-YTKYR-T4X34-R7VHC
start /w slmgr.vbs –ato
Step 4: Update the Server
Before we apply Server roles and features to the server, it is essential to update the server with the latest Windows updates.
The Server Configuration tool (sconfig.cmd) has a menu option to set Windows Update settings and an option to manually update the server. By default the Windows Update settings are set to update manually (the administrator specifies when and what updates to download and when and what updates to install).
First, let’s enter the Windows Update submenu by pressing 5 and Enter.
Press A, followed by Enter to set Windows Update to Automatic.
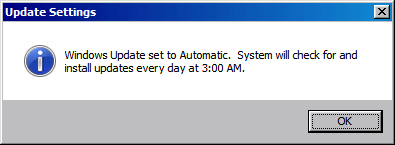
Press OK to acknowledge the change to the Windows Update settings.
Note:
If you need more granular control over Windows Update settings, specify these settings with a Group Policies, after you’ve created the domain.
To manually update the Windows Server now, press 6 and Enter in the Server Configuration Tool. Choose to search for All updates, by pressing A and Enter. After a while, choose to download and install All updates, by (again) pressing A and Enter.

After installing the Windows Updates, the box needs a restart. Press Yes to restart.
Step 5: Install the roles and features
We can now turn our Windows Server installation into a functional Server, services clients and employees with meaningful information. For the purpose of this blogpost we’ll transform this vanilla Server Core installation into an Active Directory Domain Controller.
The Active Directory Domain Services – Domain Controller role in Windows Server 2008 R2, features the Active Directory Gateway Services. This is a web service, that enables the Active Directory PowerShell cmdlets and the use of the Active Directory Administrative Center (remotely). In order to transform the server, we need to install the .Net Framework first with the following two commands:
dism /online /enable-feature /featurename:NetFx2-ServerCore
dism /online /enable-feature /featurename:NetFx3-ServerCore
After installing the .Net Framework, we’re ready to install the binaries for the Active Directory Domain Services – Domain Controller role with the following commandline:
dism /online /enable-feature /featurename:DirectoryServices-DomainController-ServerFoundation
Now, all you need to do now to make the server a Domain Controller you’ll need to dcpromo it. Unlike a Full installation of Windows Server, though, the graphical version of the Active Directory installation wizard is not available on a Server Core installation.
This only presents a minor issue, since we can use dcpromo.exe with an answerfile.
Simply start up notepad.exe on your Server Core installation and copy,paste the following information into it:
[DCInstall]
NewDomain=forest
NewDomainDNSName=demo.ogd.nl
ReplicaorNewDomain=domain
InstallDNS=Yes
ConfirmGC=Yes
DatabasePath="C:WindowsNTDS"
LogPath="C:WindowsNTDS"
SYSVOLPath="C:WindowsSYSVOL"
SafeModeAdminPassword=P@ssword
RebootonSuccess=Yes
This will create a Domain Controller for a new domain in a new forest, named demo.ogd.nl. You may change settings according to your environment. To create an answerfile for chilc domain creation, replica domain controller creation, etc. check out Microsoft KnowledgeBase article 947034.
Save the file as dcpromo.txt and use it in the following commandline:
dcpromo.exe /unattend:C:usersadministratordcpromo.txt
The system will reboot automatically. After this reboot use Notepad to open the log files:
- C:WindowsDebugDCPromo.log
- C:WindowsDebugDCPromoUI.log.
Step 6: Install additional features
Your Server Core Domain Controller might benefit from the following Server Features, when you install them. The Active Directory PowerShell commandlets, from my point of view, are essential on a Domain Controller. You might install these with the following two commands:
dism /online /enable-feature /featurename:MicrosoftWindowsPowerShell
dism /online /enable-feature /featurename:ActiveDirectory-PowerShell
While you’re at it, I recommend also installing Windows Backup and its corresponding PowerShell cmdlets:
dism /online /enable-feature /featurename:WindowsServerBackup
dism /online /enable-feature /featurename:WindowsServerBackupCommandlet
These will help you make Active Directory aware backups.
Step 7: Update the Server
With some Server Roles and Features installed, the attack surface of your Server Core installation has dramatically increased. As a best security practice, I recommend updating the server again. Run through step 4 again to make it happen.
On top of the 28 updates I got previously, I now receive an additional 5 updates.
Step 8: Run the Best Practices Analyzer
With Windows Server 2008 R2 it has become harder to install a sloppy Domain Controller. With its built-in Best Practices Analyzer (BPA) and accompanying BPA rule updates, administrators can compare their Active Directory environments with the Microsoft Best Practices.
To install the Active Directory Best Practices Analyzer, run the following commands:
dism /online /enable-feature /featurename:ServerManager-PSH-Cmdlets
dism /online /enable-feature /featurename:BestPractices-PSH-Cmdlets
Now you can use Server Manager (servermanager.msc) MMC from a Full Installation of Windows Server 2008 R2 or the Server Manager (servermanager.msc) MMC from the Remote Server Administration Tools (RSAT) on a Windows 7 member workstation to kick-off and review Best Practices.
However, you can also kick-off and review a Best Practices Analysis from the commandline of your Server Core Domain Controller. To achieve this, run the following commands:
powershell.exe
Import-Module ServerManager
Import-Module BestPractices
Invoke-BPAModel –BestPracticesModelID Microsoft/Windows/DirectoryServices
If you want to have the results in a humanly readable format on your Server Core box, ask for the output and export it to either CSV or HTML. In case of HTML, run the following command:
Get-BpaResult -BestPracticesModelId Microsoft/Windows/DirectoryServices | Where-Object {$_.Severity -eq "Error" -or $_.Severity -eq “Warning” } | ConvertTo-Html -Property Severity,Category,Title,Problem,Impact,Resolution,Help -Title "BPA Report for Active Directory" -Body "BPA Report for Active Directory <HR>" –Head "<title>BPA Report</title><style type=’text/css’> table { border-collapse: collapse; width: 700px } body { font-family: Arial } td, th { border-width: 2px; border-style: solid; text-align: left; padding: 2px 4px; border-color: black } th { background-color: grey } td.Red { color: Red } </style>" | Out-File "\demo.ogd.nlnetlogonbpa.html"
This will create a HTML file in the Netlogon folder, where you can pick it up with Windows 7 or Full installation of Windows Server 2008 R2.
Further reading
Install an Additional Domain Controller on Server Core R2
Active Directory Management with PowerShell in Windows Server 2008 R2
Implementing Windows Server Core 2008 R2 Domain Controllers
Creating a new Domain Forest on Server Core
Installing Active Directory on Server Core with an Answer File
Prepare your Domain for the Windows Server 2008 R2 Domain Controller
Installing a Read Only Domain Controller on Server Core with an Unattend File
How to Install Windows Server 2008 R2 Tutorial Series
Hardening guide for Windows 2008 R2 Domain Controller and DNS Server
 You might be interested in working with the available Server Roles in Server Core installations of Windows Server 2012.
You might be interested in working with the available Server Roles in Server Core installations of Windows Server 2012. ![]()