Posted by Sander Berkouwer on July 31st, 2012 |
0 comments With Windows Server 2012, Microsoft has changed its Server Core strategy. In short, Microsoft now focuses on the flexibility to switch the Graphical User Interface (GUI) from a full installation to a minimal shell and even further down to server core, instead of reducing the disk space needed to run the Operating System. (the ‘disk foot print’)
With Windows Server 2012, Microsoft has changed its Server Core strategy. In short, Microsoft now focuses on the flexibility to switch the Graphical User Interface (GUI) from a full installation to a minimal shell and even further down to server core, instead of reducing the disk space needed to run the Operating System. (the ‘disk foot print’)
Is this bad?
Many systems administrators will tout the advantages of a small disk foot print in the following ways:
- Faster to implement
With less data on a (virtual) disk, the Operating System can be deployed faster initially. When deploying over the network, less data needs to be transmitted, resulting in a faster deployment and also less strain on the network.
- Less hardware needed
If you need less disk space, you can use cheaper disks in your systems. When deploying virtual servers, less expensive SAN storage is needed.
- More secure
Less data on a disk results in a significantly smaller attack surface. If there’s less code in use, then less errors in code can be leveraged.
However, these three arguments are moot points.
First of all, I’ve rarely seen an admin sitting idly by a server watching it install its Operating System. If he/she is not documenting what he/she just did or already preparing next steps in the deployment process, he/she is probably checking out social media or solving another incident.
Second, disk hardware is not expensive anymore. The difference between a Server Core installation and a Full installation in Windows Server 2008 R2 is 7GB. You cannot buy physical disks in this size range. Also, on SAN storage, disk deduplication significantly decreases the factual disk foot print on the SAN itself.
The third point is a bit harder to debate, although the ‘in use’ part is the actual part of the sentence that makes the difference. While Server Core installations in Windows Server 2012 have a bigger disk foot print, a smaller percentage of that code is actually in use when you compare it to Windows Server 2008 R2-based Server Core installations. As I’ve explained in my blogpost Permanent Link to Updating Server Core and switching GUIs, a Server Core installation differs from a full installation by the amount of GUI-related features hardlinked to in the Side by Side store in the C:WindowsWinSxS folder, which in turn is linked to the C:WindowsServicingPackages folder.
Graphical
The diagrams below illustrate the differences in disk foot print between Server Core and Full installations of Windows Server 2008 R2 and Windows Server 2012:
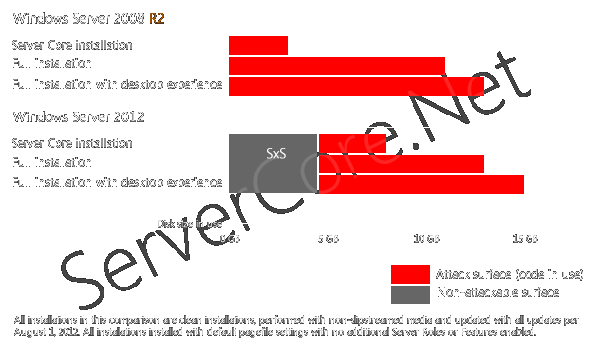
The real impact
Apart from the flexibility Microsoft is giving us to switch between the full Graphical User Interface and more minimal user interfaces, there is some real impact with Microsofts new Server Core strategy. One of the most prominent areas of impact is virtual migrations, whether they are Storage vMotions, Storage Migrations (with System Center Virtual Machine Manager), Live Storage Migrations or Shared Nothing Live Migrations: Migrating the storage for a virtual machine running Server Core will take longer, since there is more disk data to transfer.
The alternative
An alternative way Microsoft could have shaped its new Server Core strategy would be with a ‘net-install’. We see these kinds of installs regularly with Linux flavors, where the base installer is run from a setup/live disk and every add-on component is downloaded from (distributed) repositories on the web. Given the recent certificate collision attacks on the Windows Update functionality, I think it’s a good thing Microsoft decided not to pursue this idea. It will be hard to guarantee the integrity of system files when you need to get these from the web.
What do you think?
Do you think Microsoft did the right thing to hand us the flexibility of switching GUIs in the way they did it, would you go for the alternative or would you fix Server Core in a whole other way?
 A quick look at the Windows PowerShell support for Windows Server 2012 page on TechNet reveals two PowerShell Cmdlet gems for Server Core installations:
A quick look at the Windows PowerShell support for Windows Server 2012 page on TechNet reveals two PowerShell Cmdlet gems for Server Core installations: 
 The last couple of months, I ran into a lot of problems on Server Core installations of Windows Server 2012. I used the same installation media as my Server with a GUI installations, but only the Server Core installations were experiencing problems.
The last couple of months, I ran into a lot of problems on Server Core installations of Windows Server 2012. I used the same installation media as my Server with a GUI installations, but only the Server Core installations were experiencing problems.
 Last week, Microsoft has released a KnowledgeBase article titled
Last week, Microsoft has released a KnowledgeBase article titled  With Windows Server 2012, Microsoft has changed its Server Core strategy. In short, Microsoft now focuses on the flexibility to switch the Graphical User Interface (GUI) from a full installation to a minimal shell and even further down to server core, instead of reducing the disk space needed to run the Operating System. (the ‘disk foot print’)
With Windows Server 2012, Microsoft has changed its Server Core strategy. In short, Microsoft now focuses on the flexibility to switch the Graphical User Interface (GUI) from a full installation to a minimal shell and even further down to server core, instead of reducing the disk space needed to run the Operating System. (the ‘disk foot print’)